Introduction to Stream Cipher and Block Cipher
Encryption, an effective means for protecting information’s confidentiality and integrity is employed by many organizations. Symmetric algorithms play a pivotal role in secure communication and data protection – stream ciphers and block ciphers are examples of such algorithms that facilitate secure communications and data protection respectively.
Stream Cipher:
A stream cipher algorithm is a symmetrical encryption method that works on continuous data streams to encrypt it bit-by-bit or byte by byte. It uses pseudorandom keys generated using an authentic cryptographic key as inputs, creating pseudorandom streams of keys derived from these secret key values. A keystream can then be combined with the plaintext using bitwise operations like XOR to produce ciphertext – meaning the same keystream can be used both for encryption and decryption purposes.
Stream ciphers offer great efficiency and speed for data streaming scenarios such as video and voice transmission. They are more vulnerable than their counterparts to certain attacks such as bit-flipping attacks that allow an adversary to manipulate certain bits within the ciphertext and potentially affect those found within its plaintext counterparts.
Block Cipher:
Block ciphers (commonly referred to as symmetric algorithms) are encryption algorithms that use fixed-sized data blocks – typically 64 or 128-bit blocks – as part of their process for encryption. They differ from stream ciphers which encrypt bit by bit; rather they divide plaintext into blocks of fixed size before performing mathematical operations on each one with their cryptographic secrets to generate confusion by substitution, permutation, and mixing for data obscuration and diffusion purposes. Block ciphers provide high-security applications while being slower than stream ciphers due to processing data blocks of fixed size; padding schemes allow data that is outside the parameters for processing this method for handling purposes.
Stream ciphers work by using continuous streams of data to encrypt bits or bytes one at a time; making them ideal for real-time applications. Block ciphers provide greater security by breaking up encrypted chunks into fixed sizes for increased protection – these ciphers work best when used for applications that demand data integrity with high resistance against attack, deciding between block and stream ciphers dependent upon requirements specific to an application and its security requirements.
What is a Stream Cipher?
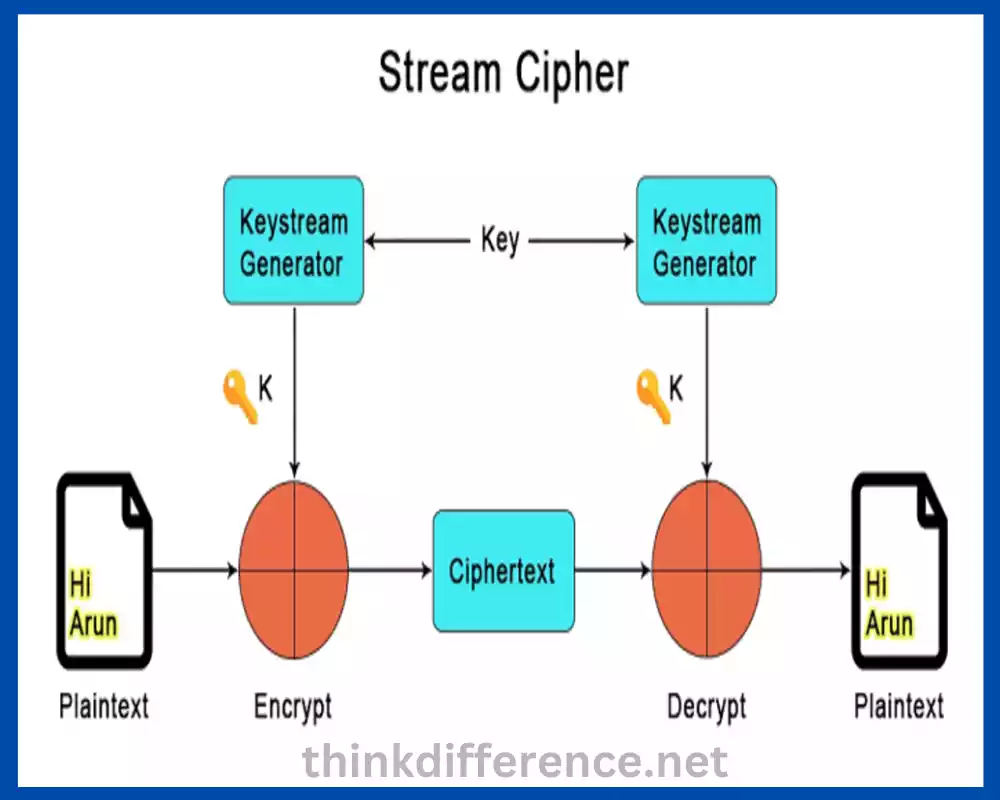
A stream cipher algorithm is a symmetric encryption method that works bitwise by encrypting individual bits or bytes at once using an individual keystream generated from cryptography secrets, followed by bitwise operations XORing them together to form the final product the ciphertext.
Stream ciphers’ signature feature is their ability to encrypt information in real-time as it arrives or leaves their destination, without breaking it up into fixed blocks of size. This makes stream-ciphers ideal for scenarios involving streaming data like voice or video communications where encryption/decryption must happen without interruption and continuity.
Stream ciphers utilize either a pseudorandom numbers generator (PRNG) or keystream algorithm for keystream generation, with PRNG using cryptographic keys to produce random bits and bytes; the key then determines what output occurs while with keystream algorithm the output remains unpredictable and statistically random, protecting encryption processes.
Stream ciphers offer many benefits that make them highly attractive options, including their efficiency. As they encrypt data bit by bit, stream ciphers are much quicker than block ciphers while continuous processing allows stream ciphers to handle data of any length without padding or additional calculations being necessary.
Stream ciphers are more vulnerable to attacks like bit-flipping due to their modular architecture and are therefore susceptible to attack vectors such as bit-flipping allowing an adversary to manipulate individual bits within the ciphertext resulting in changes to plaintext decrypted after decryption. When selecting an application-specific stream cipher it’s crucial that security requirements for decrypting are taken into consideration before selecting an encryption algorithm.
Definition and Operation
A stream cipher algorithm is a symmetrical encryption method that works bit-by-bit or byte by byte to protect information. The algorithm generates a keystream based on an encryption secret key; then uses bitwise operations (typically XOR) on plaintext data to generate the ciphertext.
Operation of Stream Cipher:
- Key Generation: A cryptographic key is generated, usually by a key generation algorithm. The key should be kept secret and shared only between the sender and receiver.
- Key Stream Generation: The key is used as input to a pseudorandom number generator (PRNG) or a keystream generator algorithm. The PRNG generates a sequence of bits or bytes known as the keystream. The keystream appears random but its generation is deterministic and depends on the key.
- Encryption Process: The plaintext data is divided into individual bits or bytes. Each bit or byte is combined with the corresponding bit or byte from the keystream using a bitwise operation, typically XOR. The result is the encrypted ciphertext.
- Decryption Process: The same keystream used for encryption is generated again by the receiver using the same cryptographic key. The ciphertext is then combined with the keystream using the same bitwise operation. As XOR is its inverse, applying XOR again with the keystream on the ciphertext recovers the original plaintext.
Keystream generation should occur simultaneously between computers, to ensure proper encryption and decryption processes are taking place. Both parties should utilize a similar key.
Stream ciphers come in different varieties. These include both synchronous stream ciphers and self-synchronizing stream ciphers; with the former type, the keystream can be created independently from both plaintext and ciphertext while with latter creates its keystream from the previous transmission’s ciphertext.
Stream ciphers offer high efficiency and are thus well suited to real-time data streaming applications. Their security is dependent on both strength and randomness in their keystream algorithm.
Advantages and Disadvantages of Stream Cipher
Advantages of Stream Cipher:
- Efficiency: Stream ciphers use rapid encryption that encrypts bits or bytes at once, making them quicker and more efficient for real-time applications that must occur instantaneously without delays in decryption and encryption processes. They, therefore, make an ideal fit for real-time environments in which encryption/decryption must occur instantaneously without delays affecting performance significantly.
- Stream Ciphers: These ciphers work well when data is being transmitted constantly, such as voice or video calls, because they allow encryption/decryption without breaking it up into blocks of fixed size.
- Data of Any Length: Stream ciphers have the unique capability of processing continuous streams of any length without padding; thus enabling encryption/decryption operations on data of any length without additional overhead costs or administrative requirements.
Disadvantages of Stream Cipher:
- Vulnerability to Bit-Flipping Attacks: Stream ciphers are more susceptible to bit-flipping attacks compared to block ciphers. In a bit-flipping attack, an attacker can modify specific bits in the ciphertext, which may lead to corresponding alterations in the decrypted plaintext. This vulnerability requires careful consideration when designing and implementing stream ciphers.
- Lower Security Margin: Stream ciphers typically have a lower security margin compared to block ciphers. The reliance on a continuous keystream and the potential vulnerabilities associated with the keystream generation algorithm can impact the overall security of the encryption process.
- Key Distribution: Stream ciphers require a secure key distribution mechanism. The same key used for generating the keystream needs to be securely shared between the sender and receiver. Security can be breached in encrypted communications if its key becomes compromised, or falls into inappropriate hands.
Even with all their disadvantages, stream ciphers can provide effective security if used appropriately and in specific scenarios. Your application’s requirements and security concerns will ultimately determine your choice between stream or block ciphers.
What is a Block Cipher?
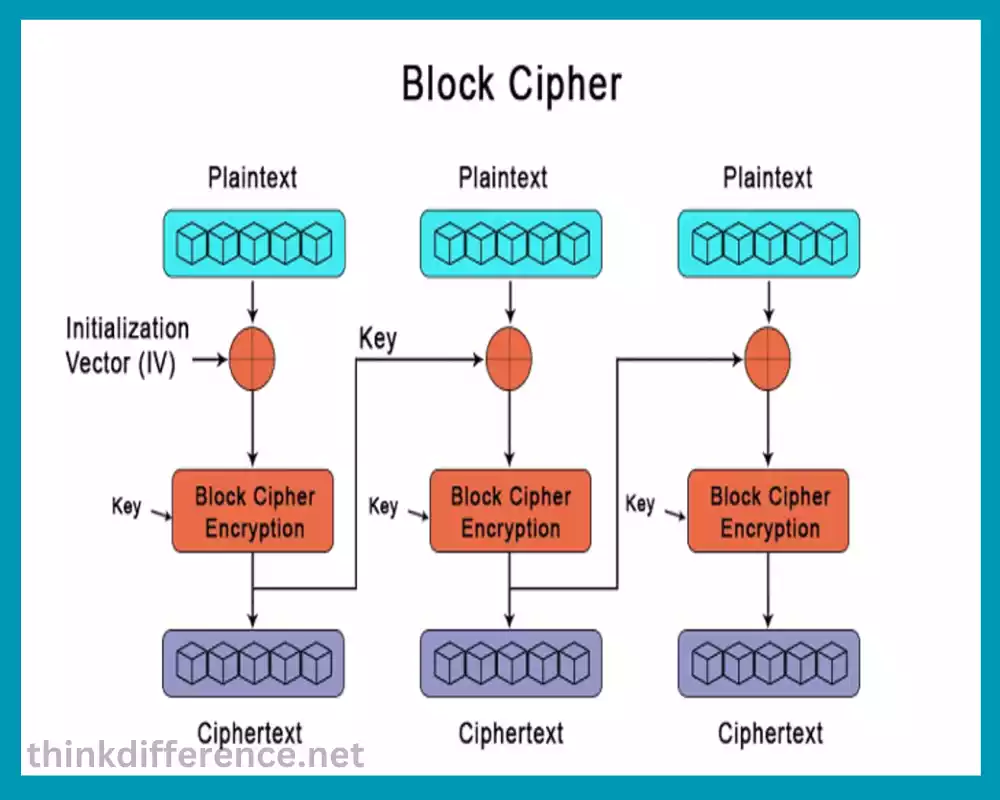
Block ciphers are symmetric algorithms that operate using blocks of fixed size; typically 64 or 128-bit size blocks of data that encrypt/decrypt independently as each key serves both for encryption/decryption processes.
Block ciphers use various cryptographic techniques such as substitution, mixing, and permutation to transform blocks of plaintext text into blocks of ciphertext. These operations are iteratively repeated over a set number of rounds by applying a round function repeatedly – usually using the current block as input and using the subkey from the primary encryption key as output to produce output for every round.
Block-cipher strength and security depend upon its round function’s complexity and security as well as the size and secrecy of the encryption key used. Some popular examples are Data Encryption Standard (3DES), Triple DES (3DES), Advanced Encryption Standard, and Blowfish Ciphers.
Block ciphers employ multiple modes, including Electronic Codebook (ECB), Cipher Block Chaining and Counter (CTR), etc. Each mode defines how blocks are linked together while providing additional security measures like preventing pattern analyses or assuring each plaintext text block has an individual ciphertext string.
Block ciphers provide privacy and integrity with numerous uses in data encryption, secure communications protocols, disk encryption, and messaging systems.
Definition and Operation
Block ciphers are symmetric algorithms that operate with blocks of fixed size to encrypt plaintext into ciphertext using an unknown secret key, typically 64 or 128-bit fixed sizes; an encryption procedure applies independently to each block during processing.
Operation of Block Cipher:
- Key Generation: A cryptographic key is generated using a key generation algorithm. The key needs to be kept secret and shared securely between the sender and receiver.
- Block Division: The plaintext data to be encrypted is divided into fixed-size blocks. If the final block doesn’t meet your exact dimensions, padding may help make it fit better.
- Encryption Process: Each plaintext block is subjected to a series of mathematical operations known as the encryption algorithm. The encryption algorithm uses the cryptographic key and transforms the plaintext block into a corresponding ciphertext block. The operations applied typically include substitution, permutation, and mixing of the bits in the block.
- Decryption Process: To decrypt the ciphertext, the same cryptographic key is used in the reverse order. The decryption algorithm applies the inverse operations of the encryption algorithm to each ciphertext block, resulting in the recovery of the original plaintext blocks.
Block ciphers operate using different modes such as Electronic Codebook (ECB), Cipher Block Chaining Counter (CTRC), etc. Each mode defines how blocks combine and provides extra security features by guaranteeing each plaintext produces unique ciphertext outputs.
Block-cipher security hinges upon factors like encryption algorithm strength, key size, and mode of operation. Modern block ciphers such as Advanced Encryption Standard(AES) have been extensively studied and utilized across numerous applications.
Block ciphers do not guarantee confidentiality for data greater than one block in length. Block cipher algorithms such as output feedback mode or counter mode may still be utilized to encrypt any length of information.
Block ciphers have many applications including disk encryption, secure communications protocols, virtual private networks (VPNs), and messaging systems with secure messaging features.
Advantages and Disadvantages of Block Cipher
Advantages of Block Cipher:
- Higher Security: Block ciphers provide greater security than stream ciphers due to their confusion and diffusion properties, making it harder for attackers to deduce patterns or extract data from the ciphertext.
- Flexible Key Sizes: Block Ciphers Are Highly Flexible When it Comes to Key Size – Block ciphers have an array of key sizes available that allow them to meet different security levels; larger key sizes resist brute force attacks more effectively.
- Security Analysis: Cryptographers have studied and scrutinized block ciphers extensively over time, leading to greater confidence in their reliability and use.
- Support for Arbitrary Data Length: Block ciphers have the capability of encrypting any length of data by breaking it up into blocks of uniform size, using padding schemes when necessary to adapt for different data lengths. This ensures compatibility across cipher types.
Disadvantages of Block Cipher:
- Slower Processing: Block ciphers tend to be slower when processing large files or communicating at high speeds, adding computational overhead when chunking data in fixed sizes.
- Bit Manipulation Vulnerability: Block ciphers may be vulnerable to certain attacks, including bit manipulation attacks by an adversary who attempts to modify bits within a ciphertext to decrypt plaintext text from it. To address these vulnerabilities and protect against them properly, extra security measures and careful implementation may be required.
- Management: Encryption relies heavily on the secrecy, integrity, and confidentiality of its cryptographic keys to achieve maximum protection for systems using block ciphers. For maximum safety, key generation, distribution, and rotation practices must adhere to regularly for maximum effectiveness in protecting the security of systems using block ciphers.
- Lack of Stream Process: Block ciphers do not perform optimally when dealing with continuous data streams due to working in fixed-size blocks, necessitating additional modes of operation like algorithms or stream cipher modes to transform block ciphers to stream ciphers.
Choose between a block and stream cipher based on the requirements of your application, such as the level of security desired, data type and performance constraints as well as compatibility issues between existing systems. Both have advantages and disadvantages that need to be assessed carefully when making this choice based on use case evaluation.
Comparison between Stream Cipher and Block Cipher
1. Operation:
- Stream Cipher: Encrypts and decrypts data continuously in real-time. Each bit or byte of plaintext is combined with the corresponding bit or byte of a keystream using bitwise operations.
- Block Cipher: Operates on fixed-size blocks of data, typically 64 or 128 bits. The plaintext is divided into blocks, and each block is independently encrypted or decrypted using a cryptographic key.
2. Encryption Speed:
- Stream Cipher: Generally faster and more efficient, especially for real-time applications or scenarios involving streaming data.
- Block Cipher: This can be slower due to the need to process data in fixed-size blocks, especially for large files or high-speed communication.
3. Encryption Security:
- Stream Cipher: Vulnerable to bit flipping attacks, where an attacker can modify specific bits in the ciphertext, potentially altering corresponding bits in the decrypted plaintext.
- Block Cipher: Provides a higher level of security compared to stream ciphers. The confusion and diffusion techniques used in block ciphers make it more difficult for attackers to deduce patterns or extract information from the ciphertext.
4. Key Distribution:
- Stream Cipher: Requires a secure key distribution mechanism to ensure the secrecy of the shared key between the sender and receiver.
- Block Cipher: Also requires secure key distribution, as the strength of the encryption directly depends on the secrecy and integrity of the cryptographic key.
5. Handling of Arbitrary-Length Data:
- Stream Cipher: Can handle data of any size without additional padding. Suitable for variable-length or streaming data.
- Block Cipher: Divides data into fixed-size blocks, which may require padding for data that is not an exact multiple of the block size.
6. Complexity and Security Analysis:
- Stream Cipher: Simpler design compared to block ciphers, but may have a lower security margin.
- Block Cipher: More complex design, with extensive security analysis and evaluation by the cryptographic community.
7. Usage:
- Stream Cipher: Well-suited for real-time applications, streaming data, or situations where data arrives continuously.
- Block Cipher: Widely used in various applications, including disk encryption, secure communication protocols, and secure messaging systems.
Block and stream cipher selection is determined by the requirements of an application, including its security level, data characteristics, performance constraints, and compatibility with existing systems. Each type of cryptography offers both benefits and drawbacks. It should only be chosen after conducting an assessment of your use case.
Popular Stream Ciphers
There are a handful of stream ciphers that have seen widespread use in cryptographic applications, here are a few notable ones:
- RC4 (Rivest Cipher 4): RC4 is one of the most well-known and widely used stream ciphers. It was developed by Ron Rivest in 1987. RC4 operates on byte-level input and generates a keystream based on a variable-length key. It has been widely used in protocols like WEP (Wired Equivalent Privacy) for wireless networks and SSL/TLS before the adoption of stronger ciphers.
- Salsa20: Salsa20 is a stream cipher designed by Daniel J. Bernstein. It is known for its simplicity, speed, and security. Salsa20 operates on 64-byte blocks and supports variable key sizes. It has been widely used in applications for disk encryption, VPN protocols, and secure messaging applications like WhatsApp.
- ChaCha20: ChaCha20 is a variant of Salsa20 developed by Daniel J. Bernstein. It offers similar characteristics to Salsa20 but with some modifications. ChaCha20 operates on 64-byte blocks and supports 128-bit and 256-bit keys. It has gained popularity and is widely used in applications such as TLS, SSH, and VPN protocols.
- Grain: Grain is a stream cipher designed by Martin Hell and Thomas Johansson. It was one of the winners of the eSTREAM stream cipher project. Grain is known for its compact design and efficiency in hardware implementations. It supports key sizes of 80, 128, and 160 bits and has been used in various applications, including secure RFID protocols and wireless communication systems.
- ISAAC: ISAAC (Indirection, Shift, Accumulate, Add, and Count) is a stream cipher designed by Robert J. Jenkins Jr. This system utilizes a pseudorandom number generator (PRNG), with 32-bit words as its data structure. ISAAC is known for its cryptographic security and is often used in software applications requiring random number generation, including cryptography libraries and gaming systems.
While stream ciphers were once popularly employed for encryption purposes, security has evolved with time and any choice should take into account current recommendations and standards for effective security measures.
Popular Block Ciphers
Various block ciphers have become widely utilized for cryptographic applications. Here are a few notable ones:
- Data Encryption Standard: (DES) was first designed and adopted as the U.S. government standard in the 1970s. Utilizing 56-bit keys and operating on blocks of 64 bits, DES had widespread adoption during that era but due to advances in computing power it is considered insecure; hence its replacement with more secure block ciphers has become widespread since that time.
- Triple Data Encryption Standard (3DES): 3DES employs two or three keys to use the DES algorithm and has increased encryption cycles compared with its counterpart, slowing it down but providing greater protection than its DES counterpart. As it offers backward compatibility benefits it has found widespread application within legacy systems and applications requiring backward compatibility.
- Advanced Encryption Standard (AES): Advanced Encryption Standard, commonly referred to by its acronym AES has become one of the world’s most acclaimed block ciphers since being adopted as a standard algorithm by the U.S. National Institute of Standards and Technology in 2001. Operating on 128-bit blocks with keys of sizes 128, 192, or 256 bits supported, AES is known for being efficient, secure, and versatile – characteristics often described as characteristics that define successful block ciphering algorithms.
- Blowfish: Blowfish was developed by Bruce Schneier in 1993 using 64-bit blocks that support key sizes from 32 bits up to 448 bits. Blowfish is known for being both simple and rapid. It remains widely popular. Though more secure solutions like AES may exist now, legacy systems still utilize Blowfish due to its simplicity.
- Twofish: Twofish was designed as an advanced encryption standard selection candidate. Utilizing 128-bit blocks with key sizes ranging between 128, 192, and 256 bits, Twofish has proven extremely secure across applications ranging from disk encryption and secure communications protocols to media streaming services and disk encryption software.
Here are several popular block ciphers. When selecting block ciphers, many factors come into play such as security, performance, and compatibility considerations. Cryptographic communities frequently evaluate and develop new block ciphers in response to changing security needs.
Hybrid Ciphers: Combining Stream and Block Ciphers
Hybrid ciphers combine both stream cipher and block cipher strength for maximum security when creating encryption schemes, providing fast and straightforward data-block encryption services that combine speed with security for fixed-size data block encrypting. Each type offers both advantages and drawbacks; with hybrids taking full advantage of each type’s strengths.
To create a hybrid cipher, the most straightforward technique involves first creating a keystream using stream cipher technology before joining it with plaintext via bitwise XOR operation (exclusive OR). Decryption can then take place using this same keystream; hence the name “stream cipher with XOR”.
Here’s an overview of how a hybrid cipher combining stream and block ciphers works:
- Key Generation: A secure cryptographic key is generated for both the stream cipher and the block cipher.
- Stream Cipher (Keystream Generation): The stream cipher generates a keystream by encrypting a randomly generated initialization vector (IV) using the stream cipher’s key. The keystream should be as long as the plaintext to ensure each bit is used only once.
- XOR Operation: The keystream is combined with the plaintext using the bitwise XOR operation. Each bit of the plaintext is XORed with the corresponding bit of the keystream. This process converts the plaintext into ciphertext.
- Block Cipher Encryption: The resulting ciphertext is divided into fixed-size blocks. Each block is independently encrypted using a block cipher algorithm, such as AES. The block cipher operates on the individual blocks using the block cipher key.
- Ciphertext Generation: The encrypted blocks from the block cipher encryption step are concatenated to form the final ciphertext.
- Decryption: To decrypt the ciphertext, the same process is applied in reverse. Recover the plaintext by XORing together decrypted blocks with keystream.
Hybrid ciphers combine elements from both stream- and block ciphers to offer effective encryption of any length data (stream cipher), while still offering increased security and flexibility with fixed-size blocks (block cipher). This approach is popularly employed by various encryption protocols and applications like SSL/TLS to secure internet communication.
Summary
Both Stream ciphers and Block ciphers are essential components of modern encryption techniques, each offering unique strengths and applications. Stream ciphers excel in scenarios requiring real-time encryption, while block ciphers provide higher security for fixed-size data blocks.
As technology evolves, new encryption methods, such as hybrid ciphers, are emerging to address the challenges posed by quantum computing. Overall, the continuous advancement of encryption ensures a safer digital landscape for individuals and organizations alike.